
A Taxonomy for Cybersecurity Control Sets

NIST CSF Review
The National Institute for Standards and Technology (NIST) Cyber Security Framework (CSF), described in a document titled Framework for Improving Critical Infrastructure Cybersecurity, is structured with 5 Functions, 23 Categories, and 108 Subcategories. The control descriptions of each category and subcategory provides a general perspective of the requirements for secure business operations. It offers ease of communication throughout an organization with the high-level categorization of controls. The recent revisions and updates among other NIST risk and security publications often refence the CSF as a structure for executive or Tier 1 reporting and decision making for framing and guidance of risk management.
A significant component of the NIST Risk Management Framework (RMF) is the family of controls found in the NIST SP 800–53r5 Security and Privacy Controls for Information Systems and Organizations publication. These controls are segmented into specific requirements within the NIST SP 800–53Ar5 document and can be used to define the remediation required to fulfil the gaps found in the risk analysis of each security control.
Definitions
CSF Breakdown into an ISCN
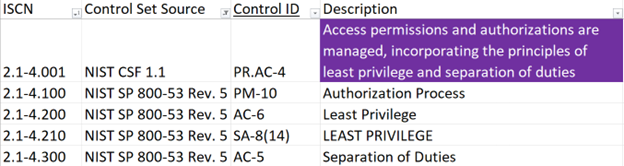
Figure 1: Alignment of controls with the ISCN
Benefits
- 1
An interface into these controls with the ISCN facilitates ease of use, flexible configuration, and consistent compliance
- 2
A referenced taxonomy of controls permits governance to be aligned with the operational implementation creating a line-of-sight from Tier 1 management to the Tier 3 operational activities
- 3
The cybersecurity taxonomy aligns controls from many sources for efficient and timely coordination within any organization and shared between third parties
- 4
Quality input from mapping with the ISCN produces indexed measurements and informative metrics when reporting on the performance of the controls
- 5
Solves an asymmetrical measurement problem when aggregating disparate scores of the security and privacy requirements
- 6
Measurements for the controls follow a consistent scaling model
- 7
Improves communication of security requirements among organizational units
- 8
The response to risk is recognized, communicated, and accurately referenced in the risk register with the ISCN identification
- 9
Reduces the redundancy of conducting risk assessments by grouping similar control elements into a single referenced taxonomy
- 10
Assignment of an ISCN for controls in policies references multiple published controls sets or the internal ITGC
Conclusion
Kent E Pankratz, MSISA & CISSP
As a Senior Manager and IT Security Analyst at SecurEnds Inc. with over 25 years of IT security experience, Kent seeks to unify control sets and accurately measure the performance of controls. SecurEnds, https://securends.com, provides the cloud software to automate user access reviews, access certifications, entitlement audits, security risk assessments, and compliance controls.

